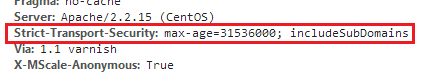
Here’s how to query non-disabled users on Active Directory. There are 2 conditions I want to set:
1. Object is of type user / person
(objectCategory=person)
2. User is active, not disabled
This is a tricky one, luckily there’s a way to use bitwise filter to find not-disabled users. The flag for disabled account in AD is 0x02 (decimal 2), hence we can create a negative condition which reverse this condition:
(!UserAccountControl:1.2.840.113556.1.4.803:=2)
The odd 1.2.840.113556.1.4.803 portion there is actually a bitwise OR operation (thanks Microsoft for making it so subtle)
So combining both condition together with (& operator here’s my final query
(&(!UserAccountControl:1.2.840.113556.1.4.803:=2)(objectCategory=person))