Came accross VirtualBox, a free & excellent virtual machine software. I decided to take it for a spin creating a Ubuntu virtual machine LAMP stack on it..
Here We Go
- Download and install VirtualBox
- Download latest Ubuntu iso installation file
- From VirtualBox create a new Virtual Machine. Select type: Linux and version: Ubuntu. On the next step you will be prompted with dvd drive containing the installaion disk, but instead just select the iso downloaded on step 2
- Go through the Ubuntu installation steps
- It’s also very helpful to install ssh server so you can ssh into your VM later on: sudo apt-get install openssh-server
Voila! You have ubuntu running on your Windows PC
Host and Guest
In virtualization realm, host indicates your physical PC (Windows 7 in my case), and guest is the virtual machine (Ubuntu). Most of virtual machine software documentation uses host and guest terminology heavily so make sure you’re familiar with it
Networking
This is where things get tricky. Virtual machine comes with virtual network adapters, and you have to do few configuration to setup connectivity between your virtual and physical adapters.
By default VirtualBox allows the guest machine to connect to the internet through NAT, so you can download data, browse internet etc. However if you want to run servers from the guest, it won’t be discoverable by the host or other PC in the host’s network immediately.
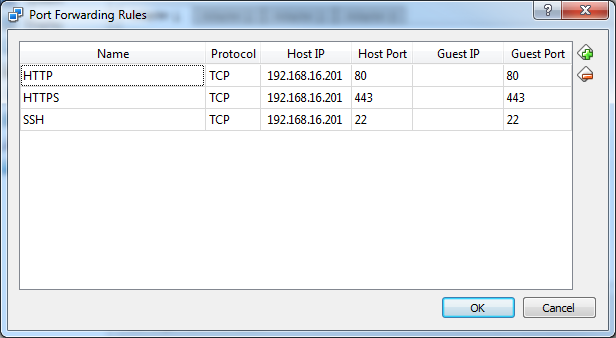
One approach to make them discoverable is by setting up port forwarding. You get here by going to networking section on the machine’s setting on Virtual Box
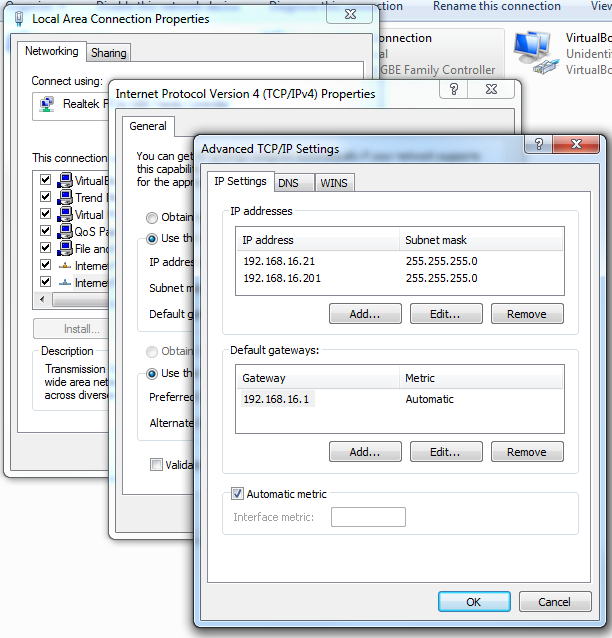
Note that setting port forwarding requires the port is actually free on your host machine. Hence I find it very useful to add an IP to your host’s network interface specifically for the VM so you don’t have port conflicts. In this example I added the IP on my interface:
The “AMP”
So there’s the “L – Linux” done. Now for the Apache, Mysql and Php, it can simply be done by using Ubuntu’s apt-get package manager:
- Open a terminal / SSH session to your Ubuntu machine
- Elevate into root using sudo su root
- apt-get install apache2
- apt-get install php5
- apt-get install mysql-server mysql-client
Few helpful notes:
- Default doc root is /var/www
- To start / stop apache: sudo service apache2 stop / sudo service apache2 start
- To start / stop mysql: sudo service mysql stop / sudo service mysql start