Eclipse is such a great tool for Java developer, but many of its feature is hidden and could be a while for a newbie to uncover it. Following is my favourite tips and tricks.
Note: The shortcuts in this post is applicable to Windows only
Type / Resource Searching
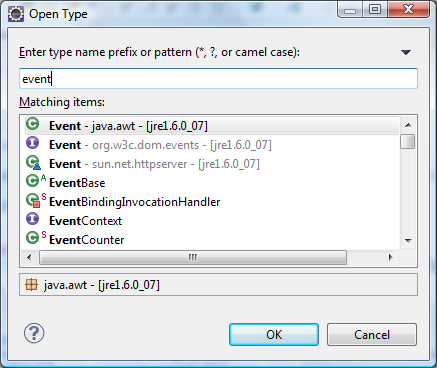
With a large project, often it’s tricky to find a particular class, XML file or other resources. Use CTRL+Shift+T to show the Open Type box, or CTRL+Shift+R for Open Resource box. Open types allows you to search for Java classes while open resources behaves more like a filesystem search, typically you would use this to look for XML, HTML, javascript, properties and so on.
You can also do wildcard searching. For example if you’re trying to find a class related to the keyword “Cat”, you can search *Cat*
Declaration /References Searching
While looking at existing program, It’s very common we need to lookup the declaration or a class or variable or search all locations where a particular class or variable is used (reference searching).
To open a declaration of a variable/type: highlight a variable or class/type reference and press F3 or right-click -> Go to declaration
To find references of a variable/type: right click a variable/type and go to the references menu
Keyboard Shortcuts
When you’re doing the same task a million times, cutting the cost of few extra mouse clicks does matter! Shortcuts in eclipse can be viewed/configured via Preferences (General -> Keys). Following are some of my favourite shortcuts:
| Action |
Windows Shortcut |
Mac Shortcut |
Note |
| Toggle comment (on highlighted text) |
Ctrl+Shift+C |
Command+C |
In java this will toggle double forward-slashes comment (//), in XML the syntax per-line |
| Toggle block comment (on highlighted text) |
Ctrl+Shift+/ |
Command+/ |
In java, enclose the highlighted text with /* comment */, in XML |
| Switch active view |
Ctrl+F7 |
Ctrl+F7 |
Allow you to switch from Editor to Console, or any other open Views |
| Switch perspective |
Ctrl+F8 |
Ctrl+F8 |
|
| Run preconfigured maven goals |
Alt+Shift+X, M |
Alt+Shit+X, M |
You can configure the maven goals via Run configuration (Run -> Run Configuration…). You have to focus on a project on the Project Explorer, or an editor window of the project’s resource |
| Run Unit Test |
Alt+Shift+X, T |
Alt+Shit+X, T |
|
* Function keys on Mac require “fn” modifier. Eg: to press F6, press fn+F6
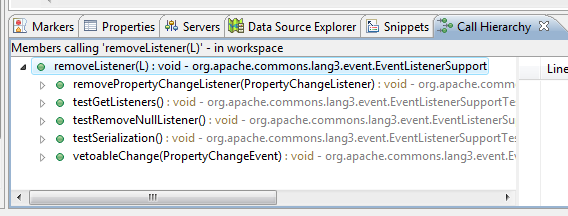
Method Call Hierarchy
This feature allows you to see what other classes calls a particular method. This is very useful when tracing down an exception, or listing the potentially impacted classes when refactoring a method.
Right click on a method, choose open call hierarchy or use CTRL+Alt+H shortcut. When you open the call hierarchy window, you can also expand each node to further drill down who called that method.
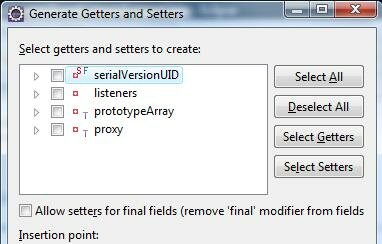
Code Generation
Eclipse came with pretty impressive code generation support. Some of my favourites are: getters/setters generators, toString generators, constructor generators, exeception try/catch block generators.
Most of this code generators feature can be accessed via Source menu or CTRL+Alt+S shortcut.
Java Code Template
If you have to include your company’s copyright policy, or some open source license header on every new java class you create, you can setup a code template. From Preferences, go to Java -> Code Style -> Code Template. On “Configure generated code and comments” select box, go to Code -> New Java files. You can insert additional comments on the top.
Configure SVN support
Eclipse doesn’t come with SVN support by default (due to some licensing restriction I think), and configuring one isn’t a straight forward task. Eclipse come with a concept of SVN provider and connector which has to be installed separately, and there are plenty possible options out there (which don’t always work).
To configure SVN support with Subversive provider and SVNKit connector:
- Go to Help -> Install New Software -> Select “Indigo” from “work with” dropdown list. This will cause Eclipse to first check all available plugins, and what has already installed (could take 15 min+)
- Open the “Collaboration” tree, and search for “Subversive SVN Team Provider”. Tick and continue with the installation process. Eclipse will ask for a restart when it’s done
- Installing the provider it’s a bit tricky. Once eclipse has restarted, open the “SVN Repositories” view by going to Windows -> Show View ->Other -> Search for SVN Repositories, and attempt to register / checkout a new repository. Subversive will realize you haven’t got any connector installed, and will show connector installation dialog. Pick the latest version SVNKit connector and install it